In this article, we are going to discuss how AppExchange works– including the security review process. At the end, you will have a clear picture of the entire process.
Before diving into the AppExchange product development, we must be aware of how the entire AppExchange ecosystem works for a successful product launch.
How does AppExchange ecosystem work?
Create – The Salesforce partner will create the business solutions.
Publish – Once the solution package is done, it will be reviewed by Salesforce and published.
Install – Business users can install the solutions from the AppExchange market.
AppExchange has a set of protocols to list your product and the product must pass the security review. It will consider the coding style and how it will protect the end-user data. Once our AppExchange solution development is done, we need to scan our product with the Checkmarx code scanner. Checkmarx is one of the leading code scanners for security and vulnerability-related stuff; Salesforce has partnered with Checkmarx.
How to use Checkmarx?
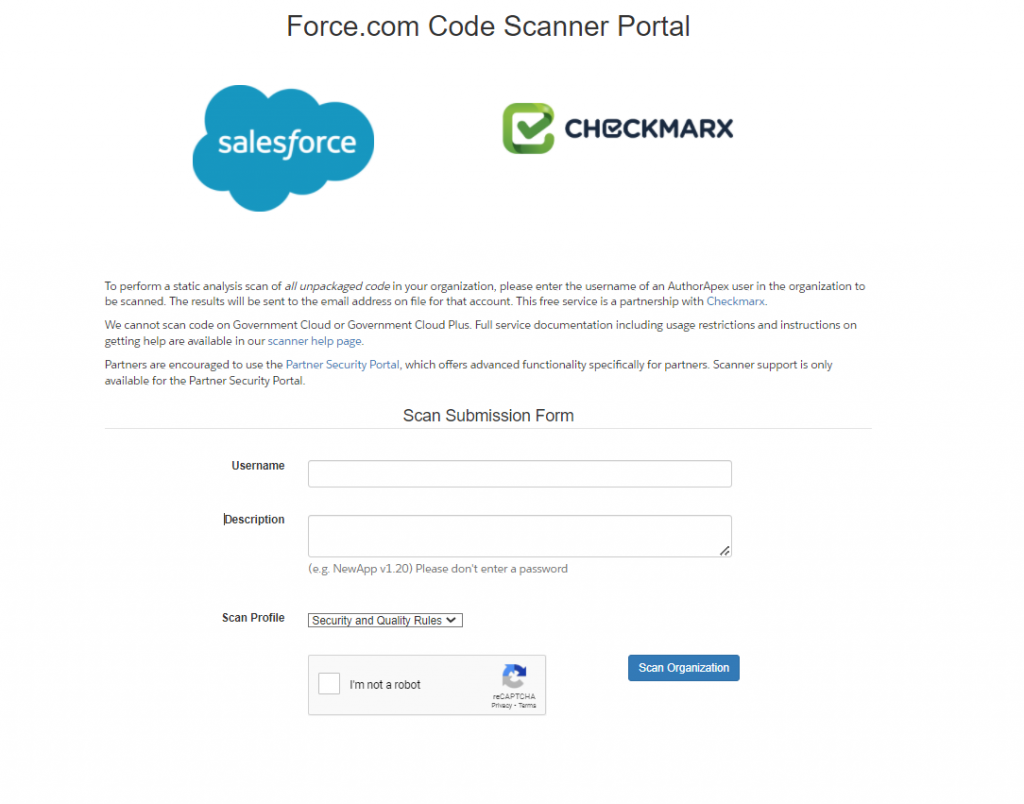
Enter your Salesforce Org username here. If you prefer to give any description, you can enter and confirm the captcha. Upon clicking the “Scan Organization” button, the tool adds your request to the scanner queue. After a couple of minutes, the corresponding org user will receive the report through mail.
Security Issues based on Group Type
The checkmarx code scanner will check your entire business logic including client side and server-side codes. Based on your code quality, best practice standards, and vulnerability, the issues will be classified.
- Apex Serious Security Risk
- Apex Critical Security Risk
- JavaScript High Risk
- JavaScript Low Visibility
- Apex Code Quality
Following are some of the common AppExchange Solution security threats based on the group type:
- Client DOM (Document Object Model) Stored XSS: JavaScript High Risk
- Multiple forms in Visualforce page
- URL Redirection Attack: Apex Serious Security Risk
- SOQL (Salesforce Object Query Language) SOSL (Salesforce Object Search Language) Injection: Apex Critical Security Risk
- DML Statements Inside Loops: Apex Code Quality
Let us discuss these issues along with a solution.
Examples:
- XSS Client DOM Stored XSS
DOM-based XSS vulnerabilities mostly occur when JavaScript takes data from an attacker-controllable source. Here, we have added an escape attribute equal to false. Be aware that putting this value to “false” may be a security risk because it allows DOM content, including JavaScript, which could be used in a malicious manner.
<apex:outputText escape=“false” value=“Terms_and_conditions__c}”/>
Solution:
<p> {!Terms_and_Conditions__c} </p>
or
<apex:outputText value=“{!Terms_and_Conditions__c}” />
- Multiple forms Issue
Sample snippet form Visualforce page
<apex:outputPanel>
<apex:form >
<apex:commandButton value=”Custom Action One” action=”{!customAction1}”/>
</apex:form>
</apex:outputPanel>
<apex:form >
<apex:inputText value=”{!customText1}”/><br />
<apex:commandButton value=”Custom Action Two” action=”{!updateCustomText1}”/>
</apex:form>
If you are using multiple forms on the same Visualforce page, we will get “Multiple forms in same page” issue.
Solution:
We should have only one form per Visualforce page. Then, add all elements inside that form tag.
- URL redirection attack
Do not hard code any URL for redirection. The following format is not a good practice.
String url = hostURL+’/’+salesforce.com/forums/?id=recordId;
If you are returning this string variable for iframe or some other redirection purpose, we will get URL redirection attack issue.
Solution
- Use page reference class for URL redirection; also you can use EncodingUtil class methods.
String url = hostURL+’/’+salesforce.com/forums/?id= EncodingUtil.urlEncode(recordId, ‘UTF8’);
PageReference redirect = new PageReference(url);
- Visualforce page with iframe redirection to other page.
- SOQL AND SOSL Injection
Below is a simple example of Apex and Visualforce code vulnerable to SOQL injection.
<apex:page controller=”SOQLApexController” >
<apex:form>
<apex:outputText value=”Enter Your Name” />
<apex:inputText value=”{!name}” />
<apex:commandButton value=”Query” action=”{!query}“ />
</apex:form>
</apex:page>
public class SOQLApexController {
public String name {
get { return name;}
set { name = value;}
}
public PageReference query() {
String qryString = ‘SELECT Id FROM Contact WHERE ‘ +
‘(IsDeleted = false and Name like \’%’ + name + ‘%\’)’;
List<Contact> queryResult = Database.query(qryString);
System.debug(‘query result is ‘ + queryResult);
return null;
}
}
Solution
To avoid SOQL injection attack, do not use dynamic SOQL queries. Instead, use static queries and binding variables for user input and concatenation. The above vulnerable example can be re-written using the static SOQL as follows:
public class SOQLApexController {
public String name {
get { return name;}
set { name = value;}
}
public PageReference query() {
String queryName = ‘%’ + name + ‘%’;
List<Contact> queryResult = [SELECT Id FROM Contact WHERE
(IsDeleted = false and Name like :queryName)];
System.debug(‘query result is ‘ + queryResult);
return null;
}
}
- DML Statement inside the for loop
In your Apex controller or trigger,do not place SOQL or DML statement inside a loop. If you did, database operations will trigger once per iteration of the loop. It will be a reason to reach the SFDC governor limits.
for (Account con : Trigger.New)
{
Contact con = new Contact (LastName = ‘Test’);
Insert con;
}
Solution
Move all the DML statements outside the loop. If you need to get any data inside the loop to perform DML operations, then use Collections.
list<Contact> conList = new List<Contact> ();
for (Account acc: Trigger.New)
{
conList.add(new Contact (FirstName=’Info’,
LastName=’Default’,
Email=’info@websitedomain.tld‘,
AccountId= acc.Id));
}
if(conList.size()>0) {
insert conList;
}
Here is some more information about the most critical web application security risks and solutions for the same. You can view them at Open Web Application Security Project (OWASP) Top Ten awareness document. (OWASP is a nonprofit foundation that works to improve the security of software)
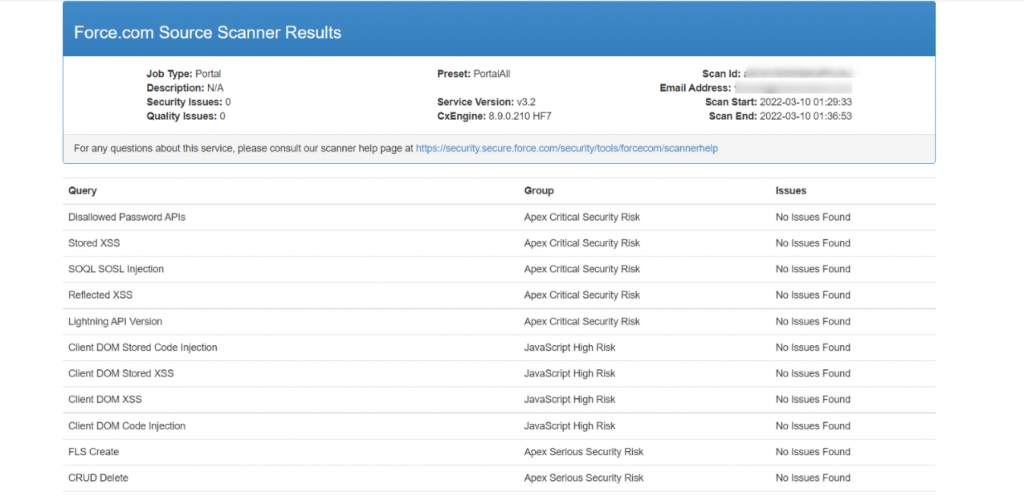
Sample Report
Sample Report Format without Issue
This is the sample report format you would receive in the email if you triggered a scan for your org. On the image displayed below, you can see the list of queries, issue group (based on risk level), and issue count.
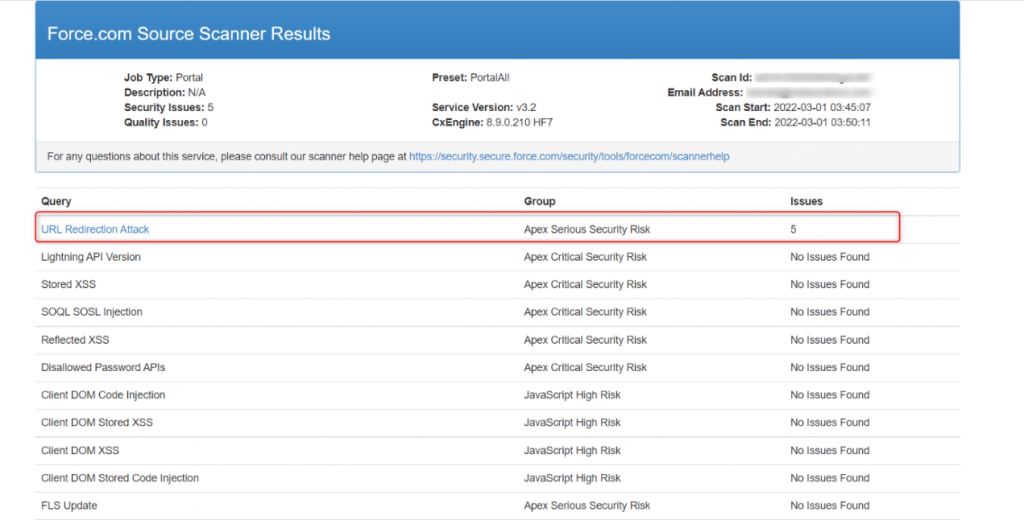
Sample Report Format with Issue
The following report has five issues related to the URL redirection attack (highlighted).
Hope you got a clear picture about how AppExchange’s review process works. Start building your solutions and have a successful launch.



